
From A to Z - A Cyber Security Glossary For B2B Marketers
Whether you are new to cybersecurity marketing or a veteran, you’ll need to talk the talk in order to walk the walk. As a marketing agency specializing in cybersecurity, marketing to hundreds of CISOs and cybersecurity professionals over the years, we’ve compiled a list of words and phrases that every B2B marketer working in cybersecurity should know by heart.
Advanced Persistent Threat (APT): A cyber attack that takes time, sophisticated resources, and expertise; typically runs against enterprises (and governments) to steal highly valuable information and monitor network activity.
Antivirus: Software used to prevent, detect, and protect computers from malware infections and threat actors.
Authentication: The process by which a computer, mobile device or network validates whether certain sign-on credentials should be allowed access.
Authorization: Refers to the scope of permissions that an authenticated user (human or machine) can see and do in the platform once access is granted.

Bot/Botnet: A bot is a software app that is programmed to perform certain automated tasks without the need for human intervention. Botnet refers to a number of internet-connected devices, running multiple bots. Despite their bad reputation, bots and botnets can be used for both legal and legitimate purposes as well as to commit cyber crimes.
A bot is a software application that is programmed to do certain tasks. Bots are automated, which means they run according to their instructions without a human user needing to start them up.
A botnet is a number of Internet-connected devices, each of which is running one or more bots
Chief Information Officer (CIO): This is the title given to the person responsible for an organization's entire technology environment. Traditionally this responsibility covered all IT functions from network architecture to providing end-user support. Today, the role has a broader responsibility to align technology with the organization's business goals and often to ensure the organization uses technology to improve its competitive advantage.
Chief Information Security Officer/Chief Security Office (CISO/CSO): CISO is a senior position, typically reporting to the CIO or CEO, responsible for protecting all technological assets from threat actors. This includes responsibility for guarding data and other valuable intangible assets stored in the organization's tech environment. Some use CSO as a synonym for CISO, but CSO more commonly describes the senior role responsible for all the organization's security needs, not just those related to technology.
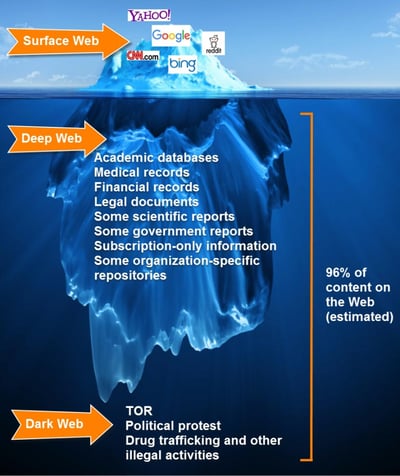
Dark Web: The Dark Web is a small subset of the Deep Web. It's a portion of the Internet not discoverable through common search engines or accessed through common browsers. Sites are encrypted and often require admin permission to access, which makes it popular with cyber threat actors.
DDoS: Distributed denial of service (DDoS) attacks are like a cousin to denial of service (DoS) attacks. In a DDoS attack, you've got a gang of online devices, known as a botnet, working together to flood a target website with fake traffic. It's like trying to drown a sandcastle with a wave of water balloons!
Deep Web: According to some estimates, not more than 1% of the Internet is discoverable by search engines. The other 99% is called the “Deep Web,” sites that aren't indexed by common search engines, and so aren’t discoverable. They can be easily accessed by anyone who knows the site's web address, however, which makes the Dark Web popular for those looking for privacy but not necessarily for nefarious activities.
DevSecOps: DevSecOps is short for "Development, Security, and Operations". The idea behind DevSecOps is to make everyone accountable for security. IT Security must play an integrated role in the full life cycle of software development and application. DevSecOps teams are responsible for introducing security earlier in the life cycle of software development in order to minimize vulnerabilities.
Digital Risk Protection (DRP): This is a set of practices and methodologies designed to safeguard an organization's digital infrastructure against digital threats. This includes but not limited to cybersecurity.
Emulator: Hardware and/or software that replicates exactly another computer system. The emulated environment can operate exactly as the original computer with full authenticity.
Endpoint security: Endpoint security refers to securing the various endpoints on an enterprise network, defined as end-user devices like desktops, laptops, tablets, and mobile devices, from unauthorized access and potential malicious attacks.
Fraud attacks: An umbrella term for cyber criminals running financial scams using stolen consumer data or manipulating vendor data.
Hacktivist: [Hacking + Activism] Anyone or group using hacking to advance their social, political or religion motivated agenda. Hacktivist tactics range from commandeering and defacing a website, like when “Malas” ransomware group hacked into the server of Zimbra, and demanded a charitable donation in exchange for not leaking sensitive information, or when Anonymous’ carried out attacks against Russia, in light of its invasion of Ukraine.

Identity and Access Management (IAM): Collection of business rules, security tools, policies, and system configurations that define the scope of privileges a specific user has to access network resources, applications, or networks, or perform a certain function on the company’s network. It aims to facilitate the management of established identities.
Insider Threats: Like insider trading, insider threats come from people who misuse their authorized access to critical information, computers, or networks; misuse can mean sharing their login credentials with threat actors or using their access to engage in a cyberattack themselves. This person does not necessarily need to be an employee – third party vendors, contractors, and partners could pose a threat as well.
Internet of things (IoT): IoT is like a club where devices like smartphones, laptops, and smartwatches chat, share data, and party together over the internet or other networks. In the world of cybersecurity, it means a bigger playground for hackers to sneak in and attack.
Machine Learning (ML): Machine learning, part of AI, is like a cyber Sherlock Holmes evil twin in the making. It learns from data and algorithms, mimicking our brains' smarts to up its game in the world of cyberattacks, making attacks much harder to detect.
Natural Language Processing (NLP): NLP is the cool tech that teaches computers to talk and understand us humans better. In cybersecurity, it's like having an extra set of ears and eyes that can spot cyber threats hidden in the chatter.
Passive attacks: An attack characterized by the attacker monitoring and sometimes scanning for open ports and vulnerabilities for the sole purpose of gaining information. In a passive attack, the intruder/hacker does not attempt to alter the system or change data.
Passwordless authentication: This is a method for confirming a user's identity without relying on a password. Instead, it employs more secure options such as possession factors (like one-time passwords or registered smartphones) or biometrics (such as fingerprints or retina scans).
Some say going passwordless is a win-win! It beefs up security, no more stressing over password breaches and stuff. Plus, it's a breeze for users – quick access without the hassle of resetting forgotten passwords.
Penetration testing: This method is used by cyber security professionals to identify vulnerabilities that hackers could use to exploit a network they aren't authorized to access. The purpose is to find and close the vulnerabilities before the hackers do. Can be performed manually or automated with PenTesting tools.
Pharming: A scam where threat actors put up a website identical to one that ultimately provides access to confidential information, like a bank or eCommerce site. Users tricked into using the pharming website enter their confidential login information, which is then used by threat actors to access the victim's account on the real website.
Phishing: A scam, generally carried out via email, where people are "baited" into providing confidential information that can then be used by the threat actors to access an account or engage in identity theft. "Spear phishing" is a targeted type of phishing where the attackers use personal or confidential information about their target to increase the likelihood of duping the mark.
Ransomware: A malicious software that denies the owner access to their computer data until the owner pays a ransom. Ransomware can come in many shapes and sizes. A particularly vicious type of ransomware is when a victim pays the ransom and is still denied access. Sometimes, even if access is regained, the attacker can still sell the data on the Dark Web.

Remote Access Trojan (RAT, AKA creepware): This type of malware allows threat actors to take complete control of the victim's computer or network for the purpose of performing malicious activities. RATs operate in a stealth mode, are often disguised as legitimate software, and are usually rather small so as to avoid detection.
Risk Management: The approach an organization takes to assess, identify, prioritize, avoid, and respond to various risks. As risks constantly evolve, risk management is an ongoing process for organizations.
Rootkit: A malware used by a hacker that hides its presence by activating itself before the OS boots up. A rootkit is typically installed through a stolen password or by exploiting system vulnerabilities without the victim's consent or knowledge.
Social Engineering: Social engineering is like the art of digital persuasion. It's when bad actors use psychology to con users into making security slip-ups or revealing sensitive info. It's basically Jedi mind tricks for hackers!
Spoofing: Spoofing is when a threat actor impersonates a user or device to steal data, spread malware, or bypass access controls. For example, email spoofing is the creation of emails that appear to be from a trusted entity that will trick readers into clicking or downloading malware, or accessing a malicious website.
SQL Injection: SQL injection, or SQLI for short, is like the sneaky ninja of cyberattacks. It uses crafty SQL code to sneak into a website's database, grabbing info that should've stayed hidden. Data, like top-secret company stuff, user lists, or customers' secrets, can all be at risk.
Steganography: Ever heard of digital hide-and-seek? That's what steganography is all about. It's the clever art of disguising one message within another to dodge snooping eyes. You can stash away text, pics, vids, or sounds, and only reveal 'em when you're good and ready.
Trojan: Named after the Trojan Horse of antiquity, "trojan" is the descriptor for any file or program that looks legitimate but is in fact malware, causing harm to a computer once activated.
Zero Trust/Zero Trust Security: A security approach that assumes everyone and everything is a threat actor until proven otherwise. It implements the strictest identity verification protocols. The original Zero Trust concept was developed by former Forrester analyst John Kindervag, and is based on the motto “Never trust; always verify.”

Zero-day attacks: The moment and means by which a network vulnerability previously unknown to the network owner is exploited by hackers. Threat actors release malware before a developer has an opportunity to create a patch to fix the vulnerability.
Did we miss anything? Don’t worry, marketing for cybersecurity companies comes with its perks, like always talking to cybersec experts and being exposed to new trends and updates. We’ll continue updating our glossary regularly, so stay tuned. Feel free to be in touch to talk about how we can partner up to boost your cyber security marketing ROI.
Or to just say "hi," that's nice too.





